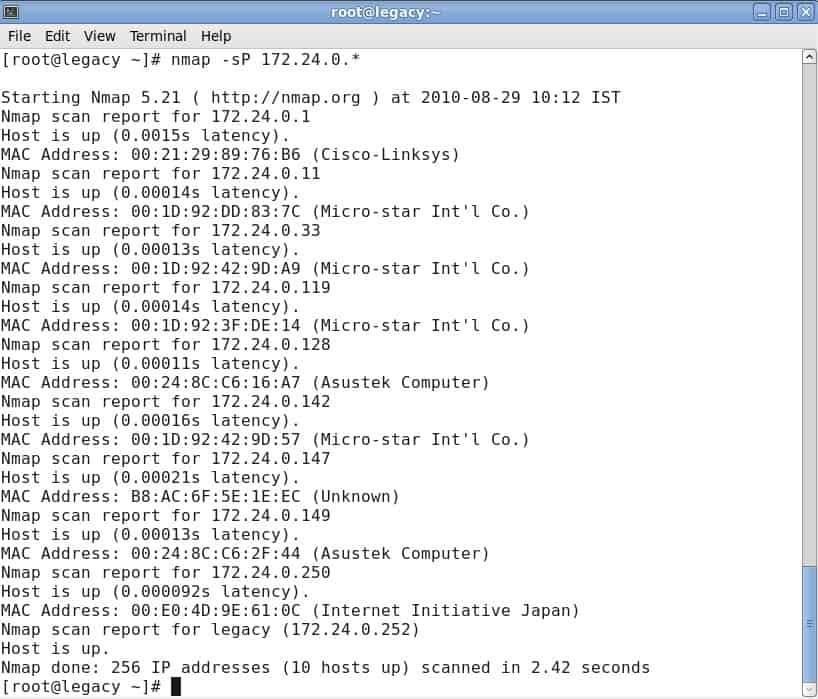
Nmap cheat sheet: From discovery to exploits, Part 3: Gathering additional information about host and network | Infosec Resources
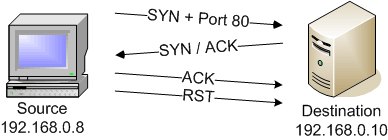
Optimizing Your Nmap Scan: Nmap Scanning Methods - Professor Messer IT Certification Training Courses
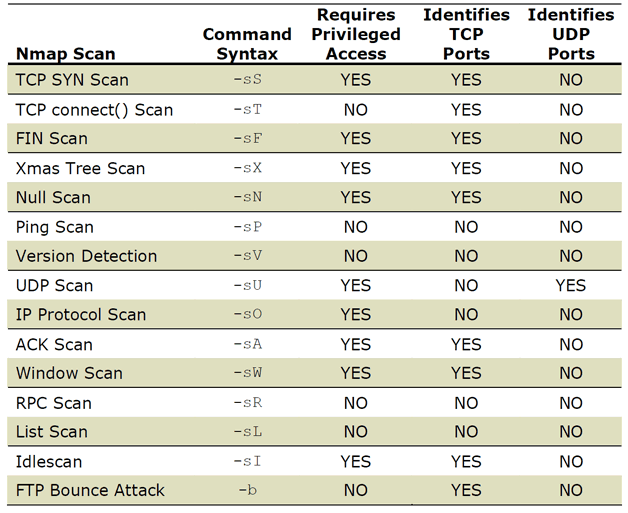
Optimizing Your Nmap Scan: Nmap Scanning Methods - Professor Messer IT Certification Training Courses

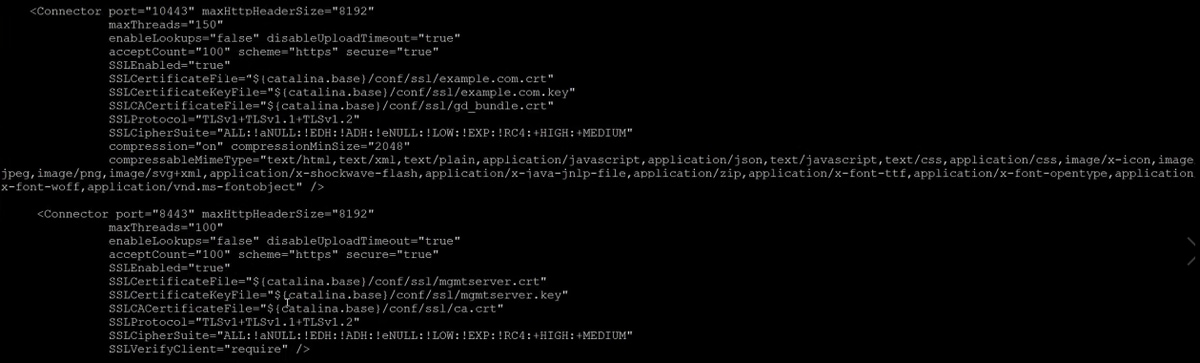


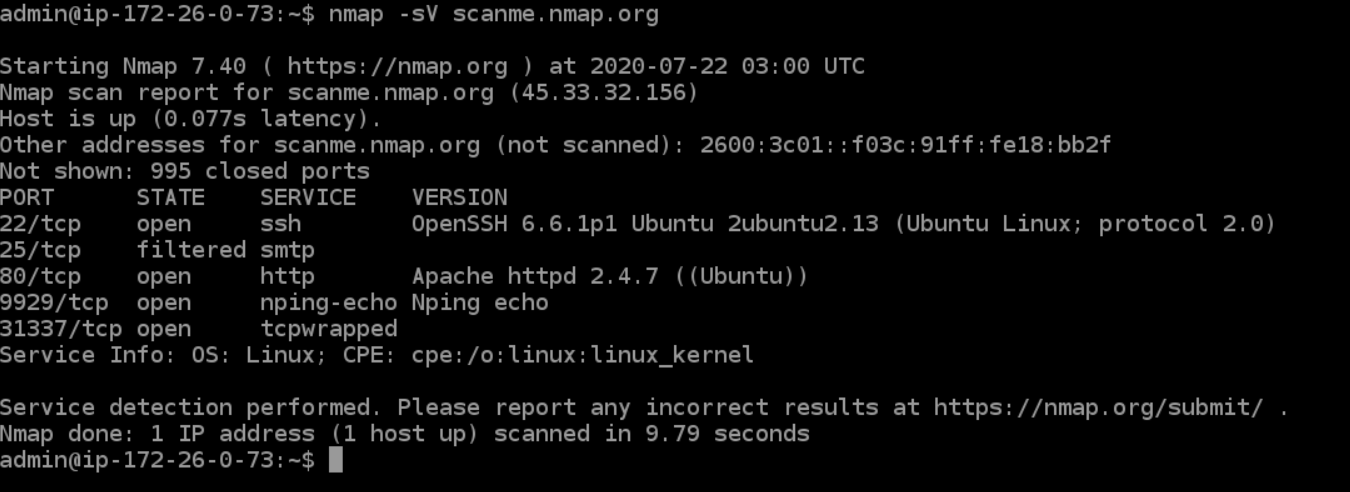
.jpg)
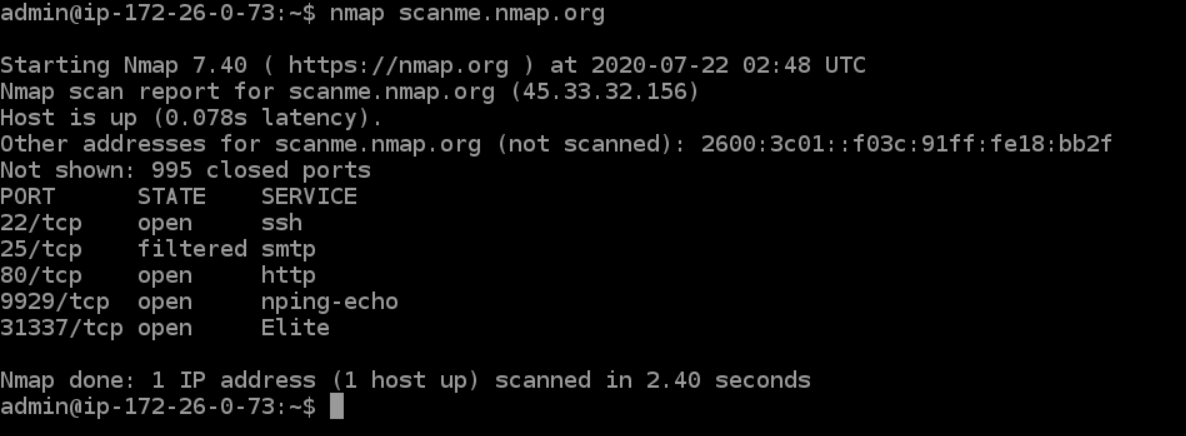
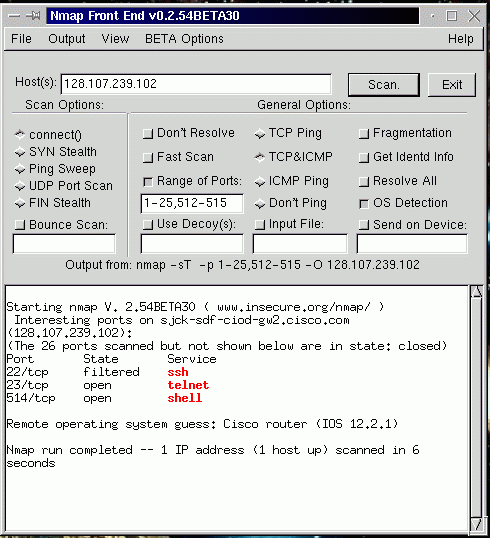

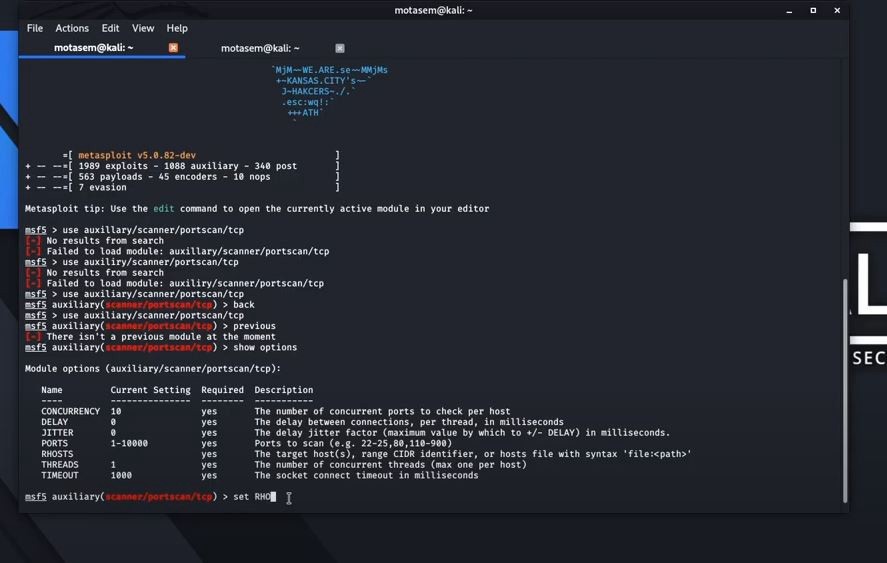
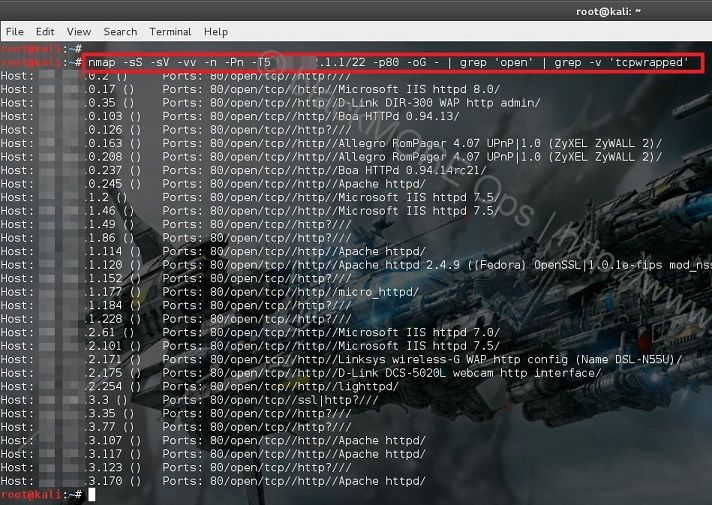
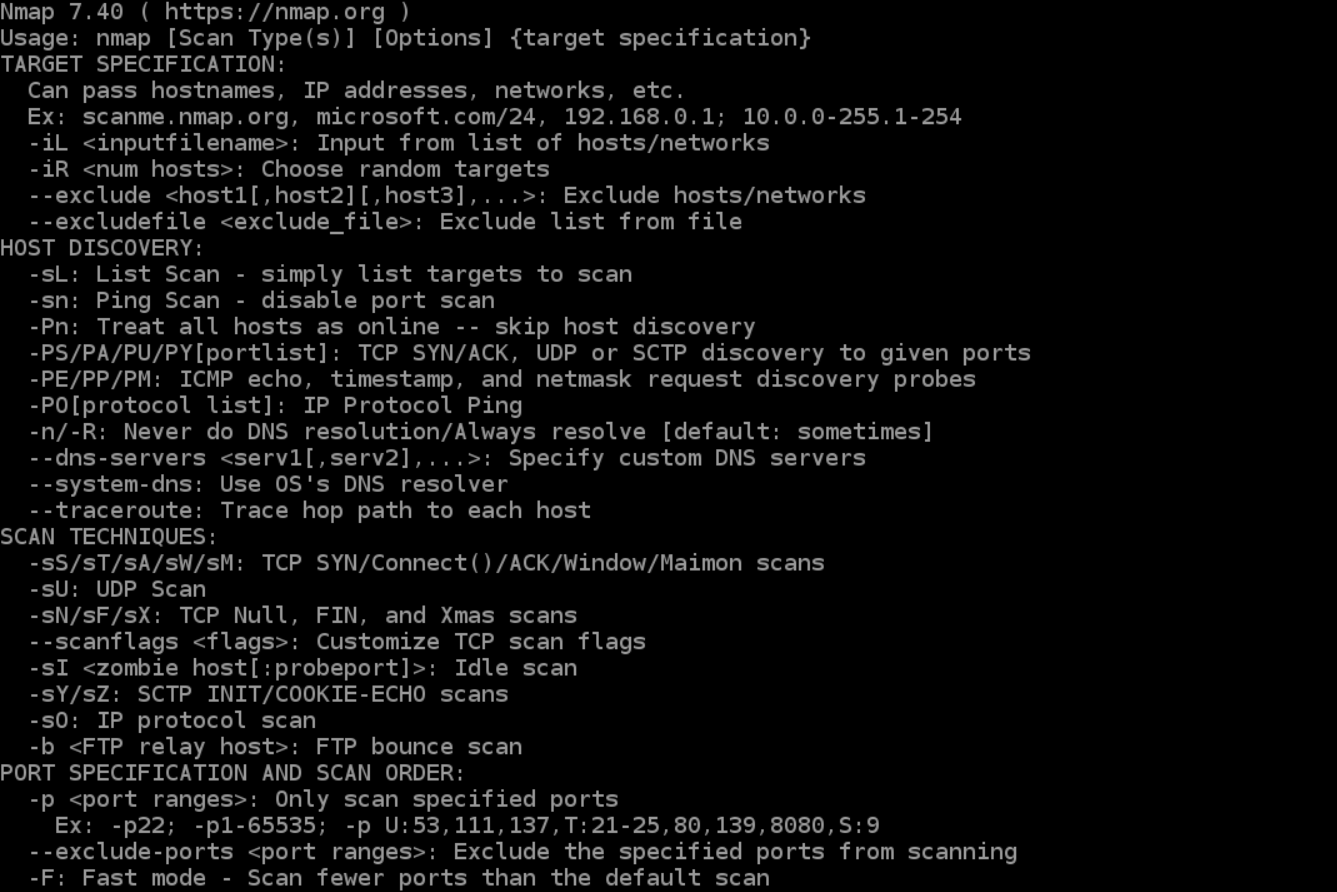
![Nmap evade firewall and scripting [updated 2019] | Infosec Resources Nmap evade firewall and scripting [updated 2019] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/082912_1952_NmapEvadeFi1.jpg)