
Llano Phone Stand Tablet Stand Desktop Stand Foldable And Portable Adjustable Height 360 Rotation Suitable For 4 12 Inches Phones And Tablets | Save Money On Temu | Temu
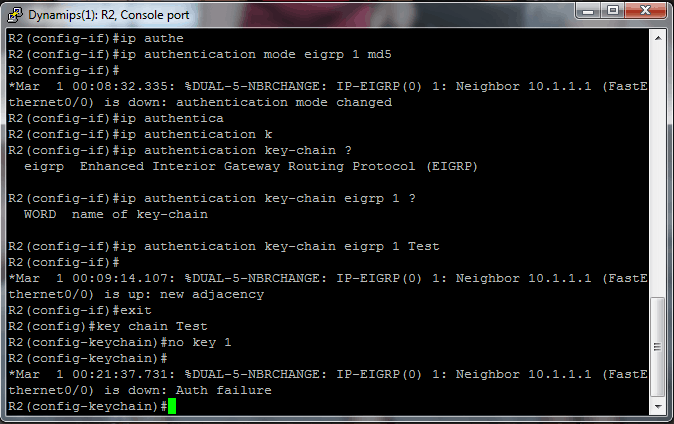
Cisco EIGRP authentication – what is the key? | Interface Technical Training | Interface Technical Training

NETGEAR RAX10 - wireless router - Wi-Fi 6 - Wi-Fi 6 - desktop - RAX10-100NAS - Wireless Routers - CDW.com














![Cisco OER Master Controller Engine GUI [Support] - Cisco Systems Cisco OER Master Controller Engine GUI [Support] - Cisco Systems](https://www.cisco.com/en/US/i/100001-200000/110001-120000/116001-117000/116687.jpg)




